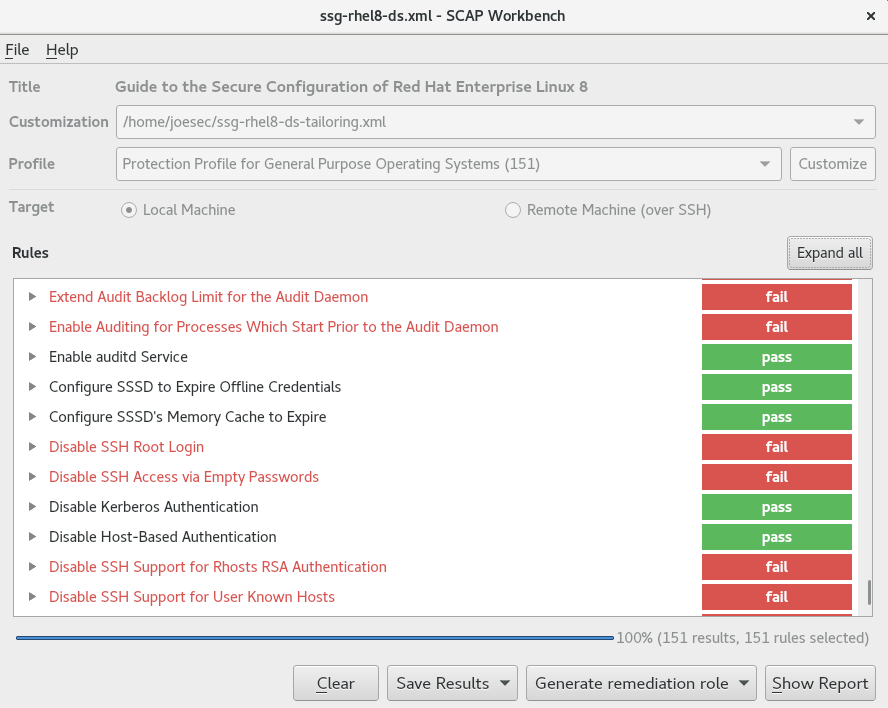
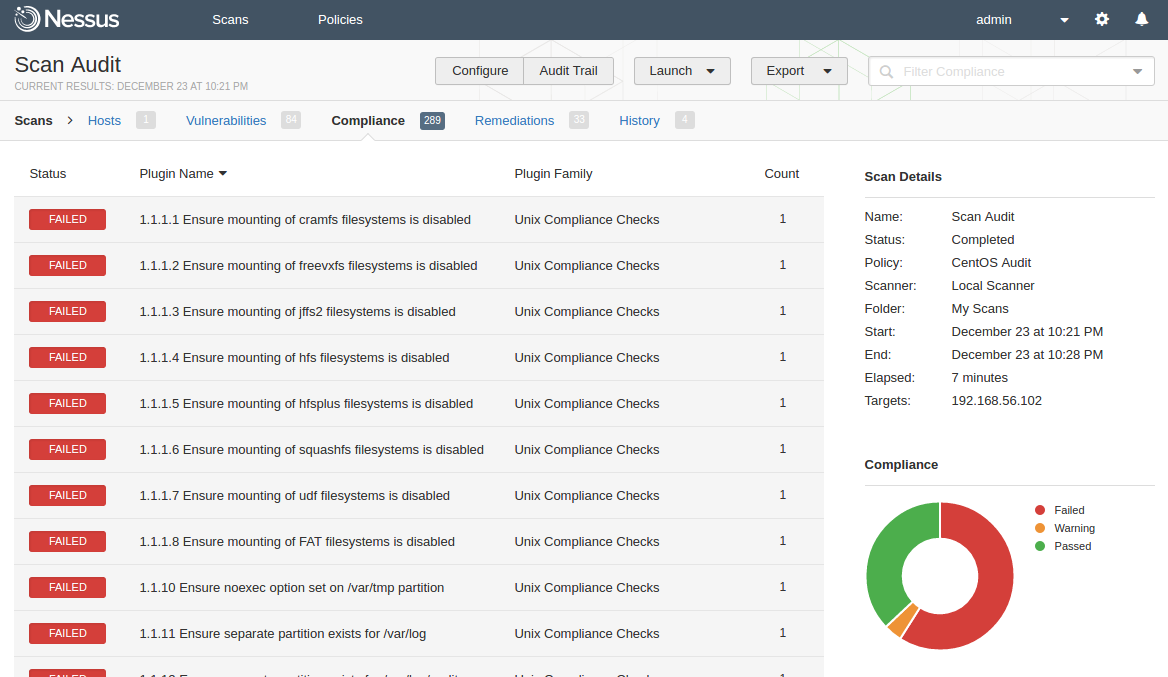
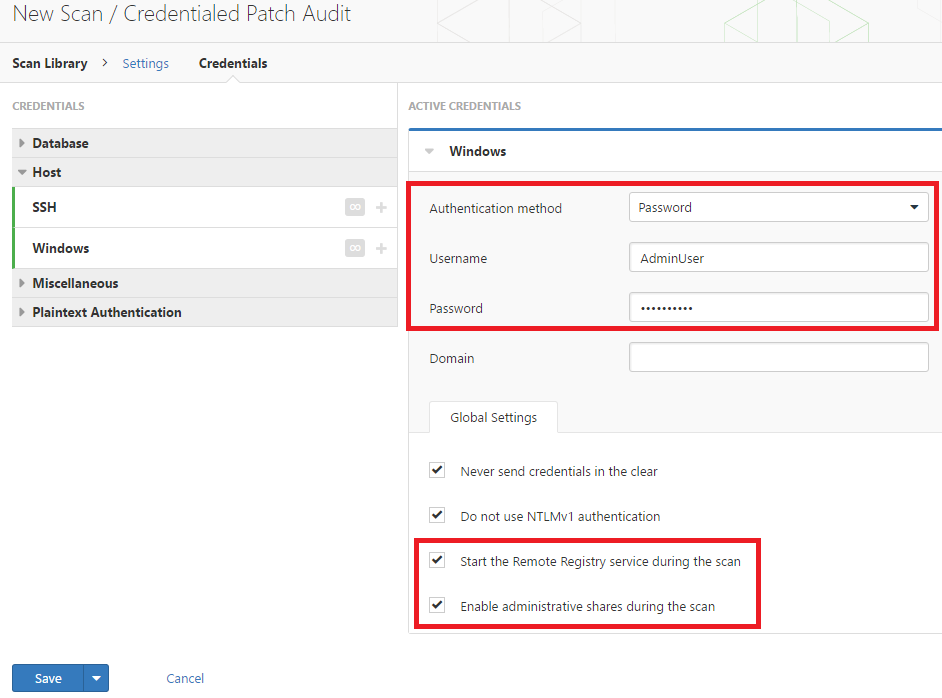
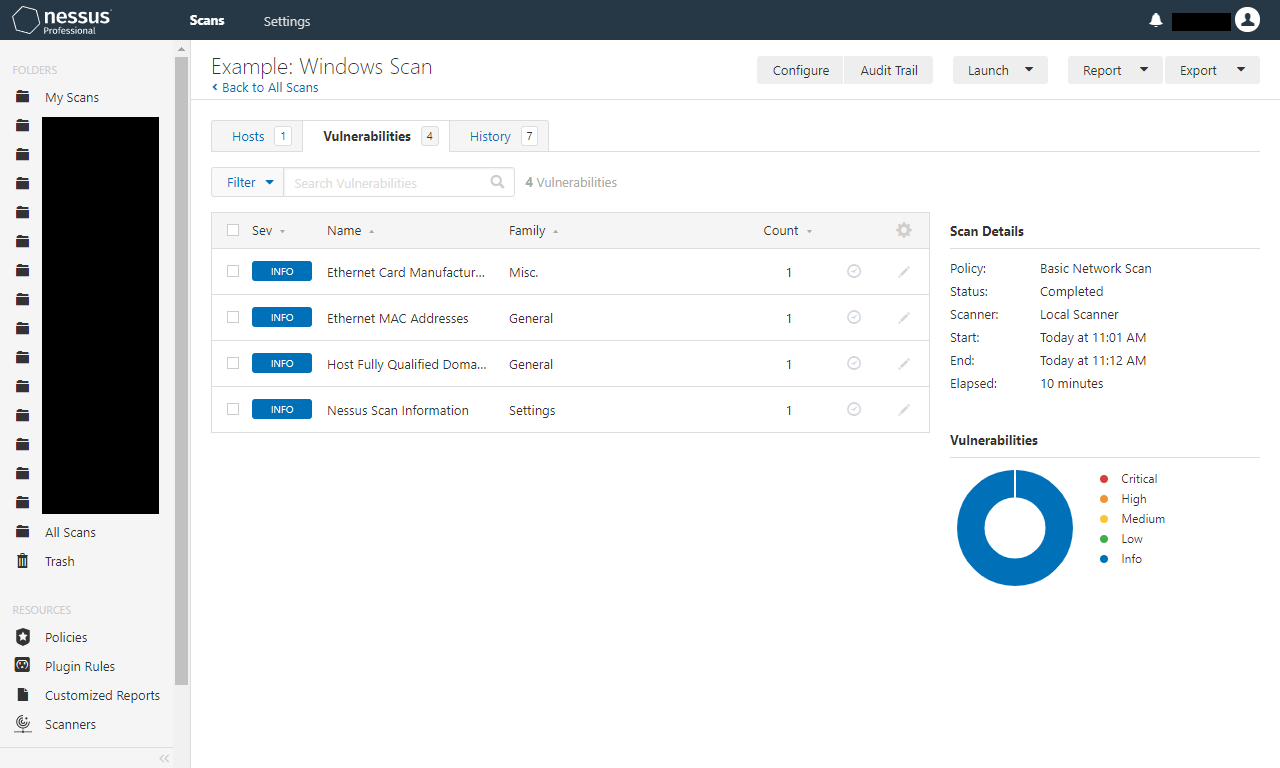
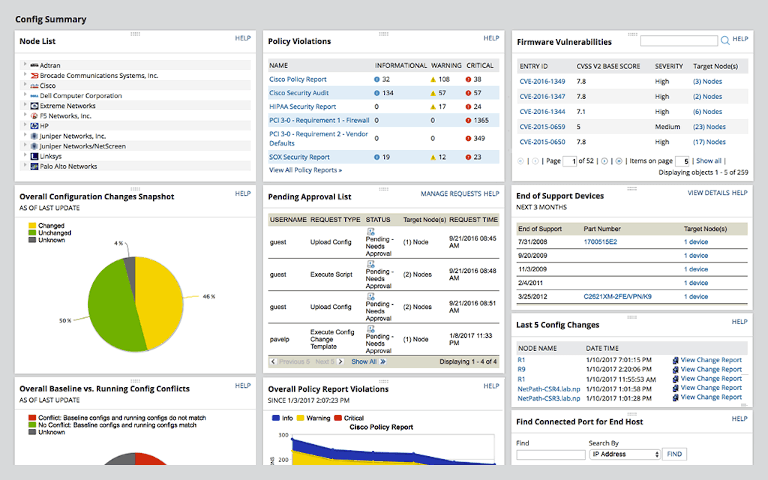
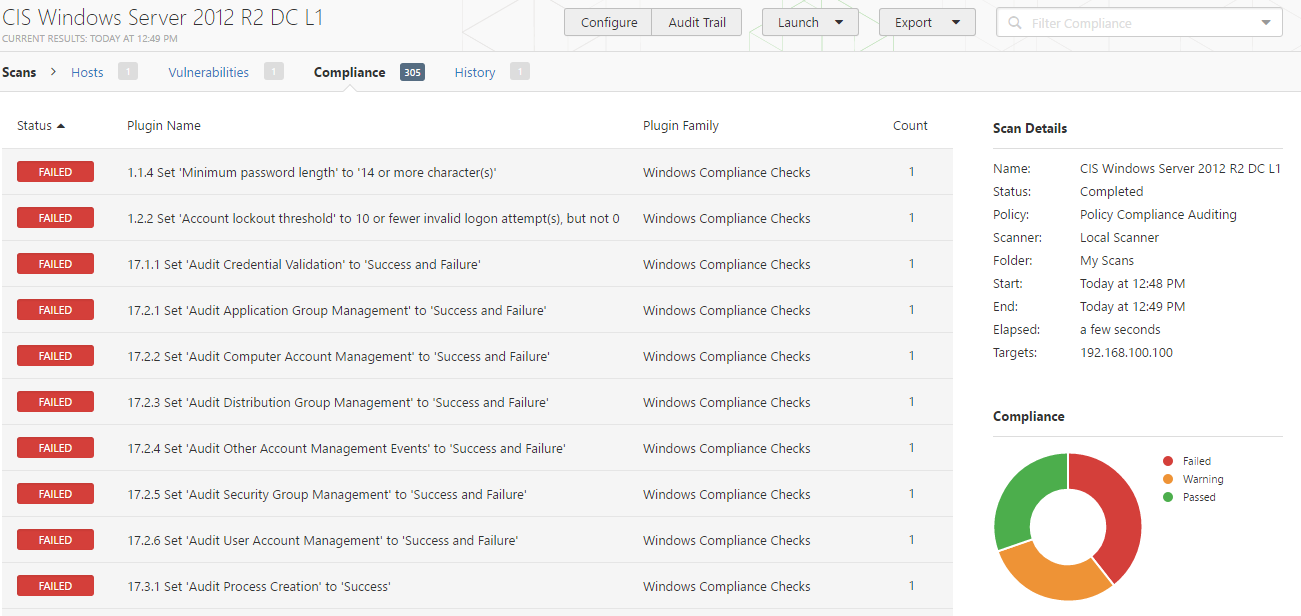
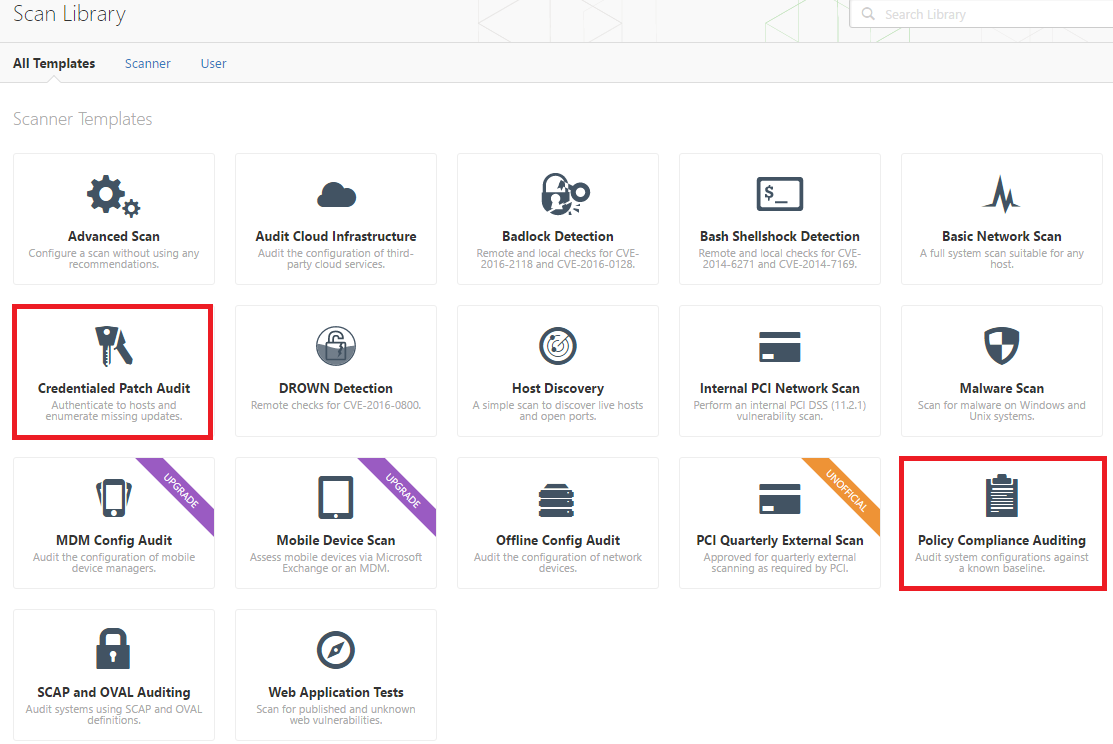
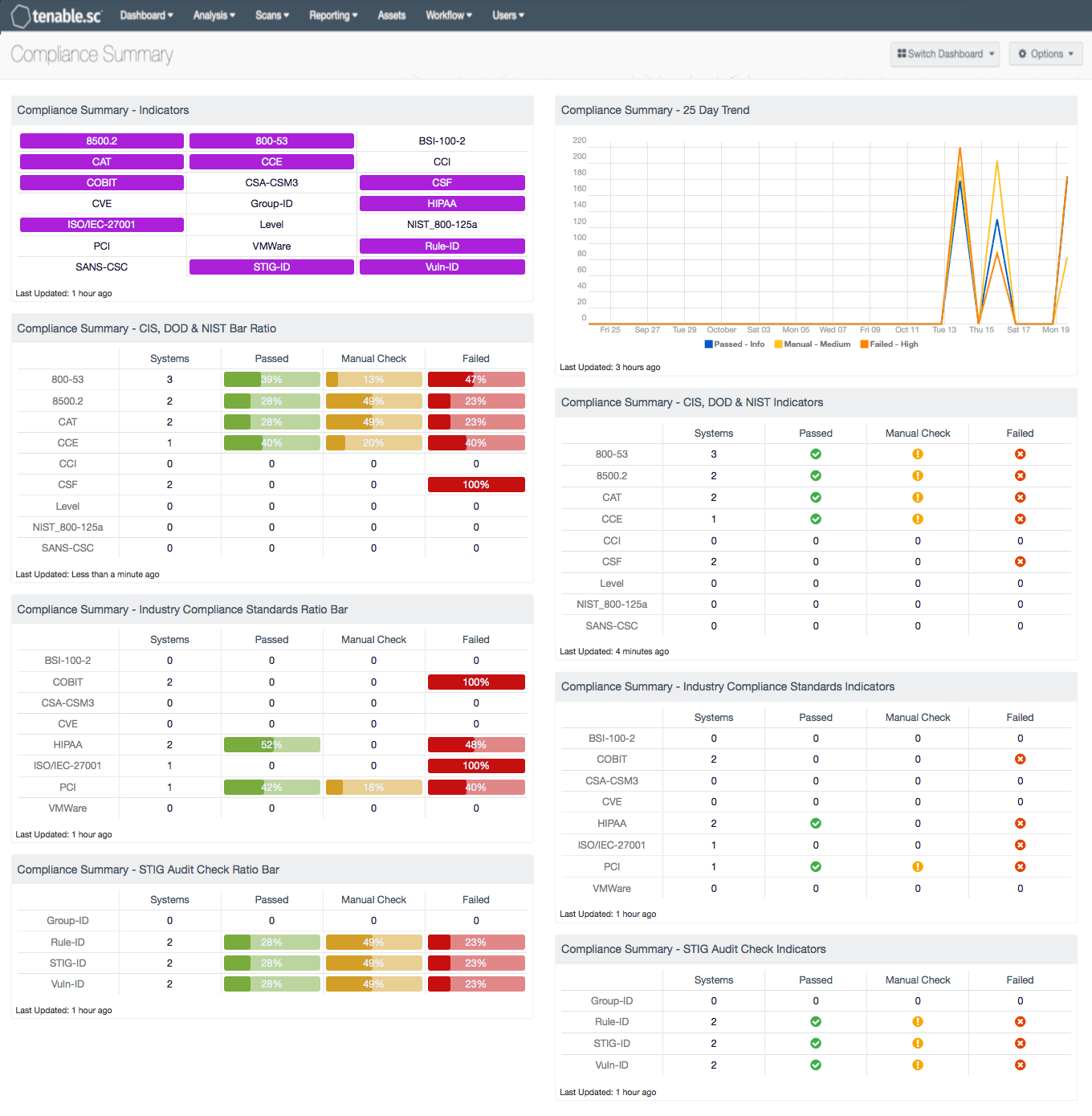
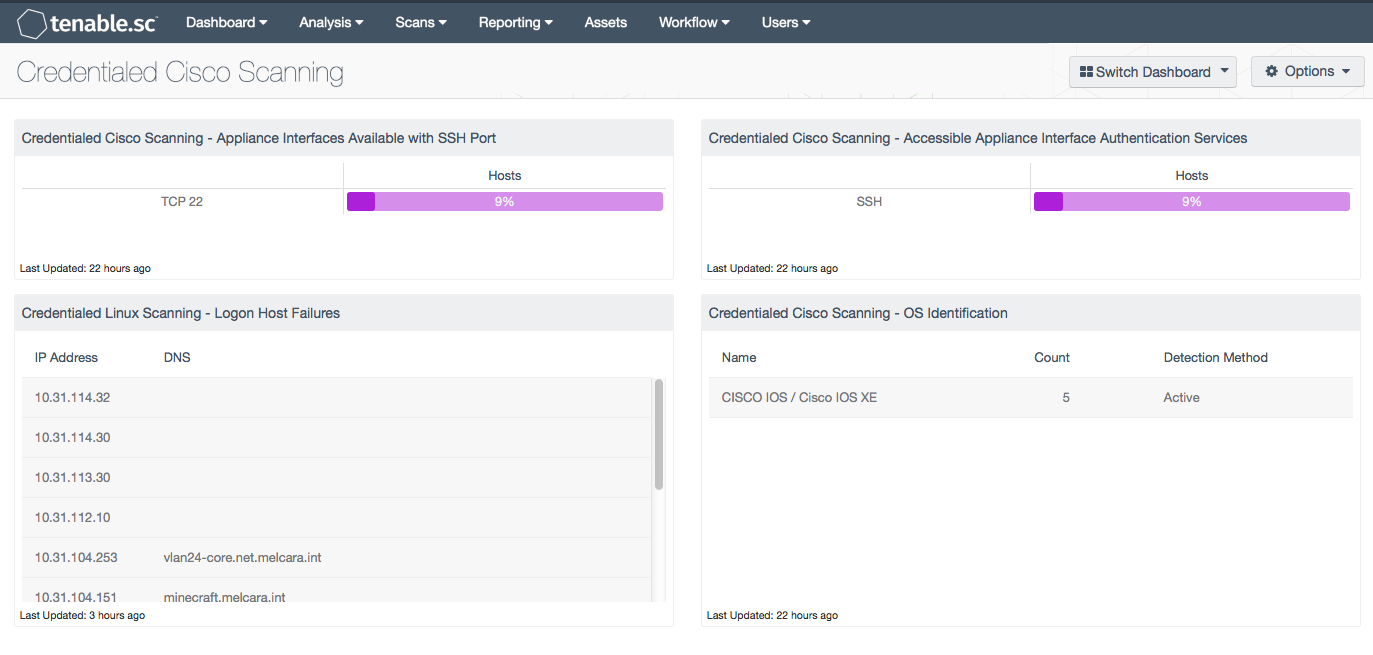
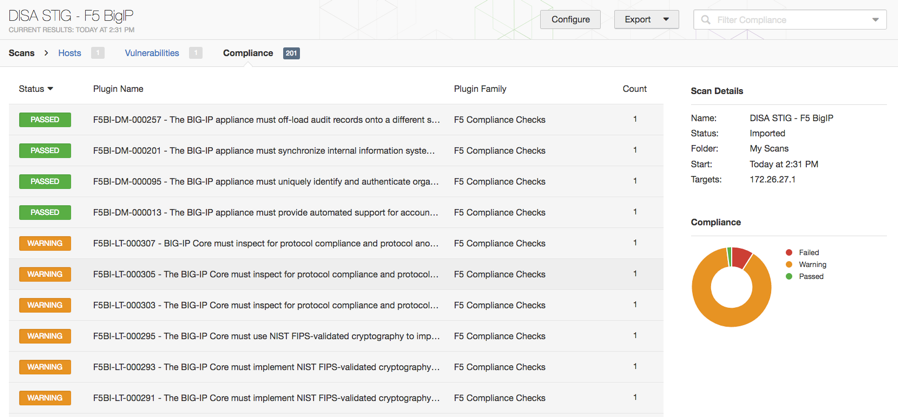
Qualys FreeScan service expanded with vulnerability scanning and configuration auditing - Help Net Security
Vulnerability Scanner | Vulnerability Scanning Tools & Software - ManageEngine Vulnerability Manager Plus
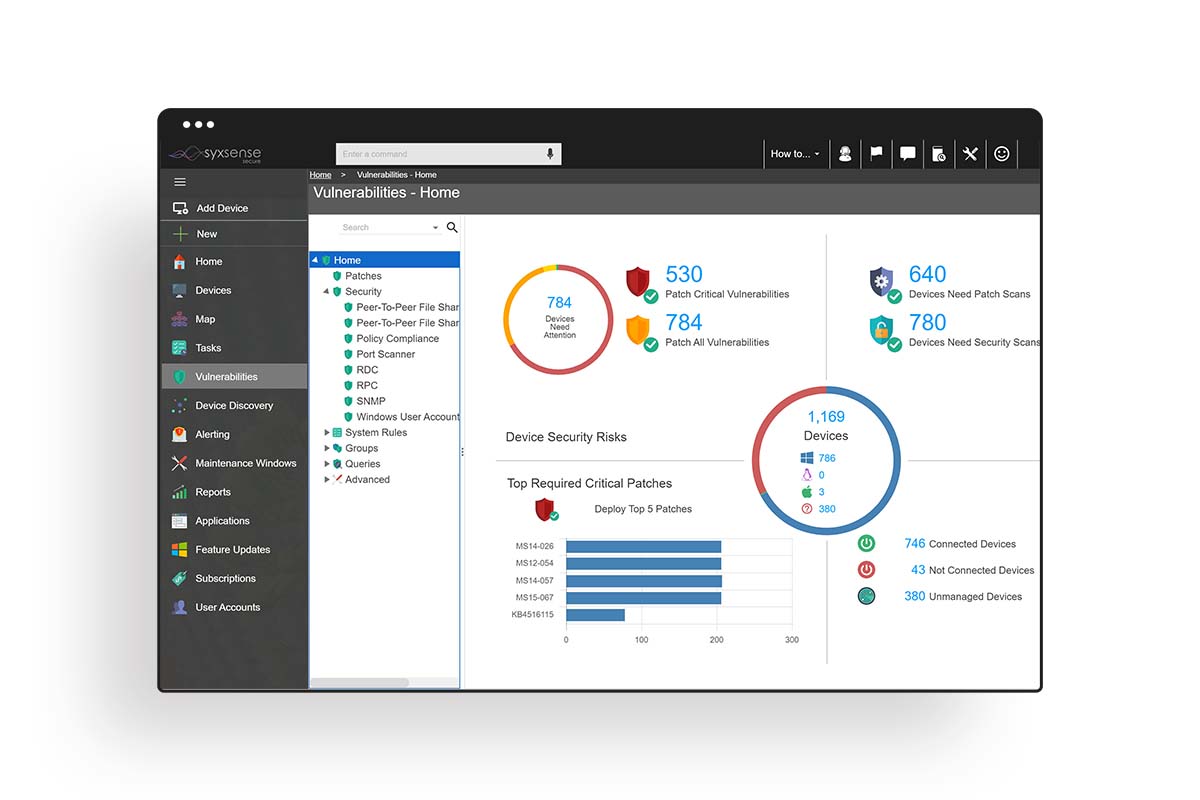
Syxsense Secure First to Unify Patch and Configuration Management with Vulnerability Scanning - Cybersecurity Excellence Awards